Create An AccessPoint Startup Script
We have one more prerequisite before we can continue. We need to create a network bridge so the access point can connect to the NAT'ed ethernet adaptor. If its not already installed go ahead and install bridge-utils.
> sudo apt-get install bridge-utils
In your home folder create a file named startAP.sh and enter the following text.
#!/bin/bash
# stop the network manager
stop network-manager
#create the bridge and add eth0
brctl addbr br0
brctl addif br0 eth0
#Start the Access Point
hostapd -B ./rtl_hostapd.conf > /var/log/hostapd.log
# wait for AP to come online before adding it to the bridge
sleep 5
#Add the wireless AP to the bridge
brctl addif br0 wlan0
dhclient br0
Run your script.
> chmod 755 ./startAP
> sudo ./startAP
In your home folder create a file named startAP.sh and enter the following text.
#!/bin/bash
# stop the network manager
stop network-manager
#create the bridge and add eth0
brctl addbr br0
brctl addif br0 eth0
#Start the Access Point
hostapd -B ./rtl_hostapd.conf > /var/log/hostapd.log
# wait for AP to come online before adding it to the bridge
sleep 5
#Add the wireless AP to the bridge
brctl addif br0 wlan0
dhclient br0
Run your script.
> chmod 755 ./startAP
> sudo ./startAP
*NOTE: ensure the birdge=br0 is somewhere in your hostapd config file.
You should now have a fully configured Wireless access point. Try to get you mobile device or other computer to connect to the internet through this access point. In some instances you will have to manually add your IP address on the device. Usually setting something like the following will work:
IP Address: 10.0.2.17
SubnetMask: 255.255.255.0
Router: 10.0.2.2
DNS: 8.8.8.8
Mallory Installation Steps
In the virtual machine that was created in Part 1 you must drop to a terminal and first install mercurial before anything else.> sudo apt-get install mercurial
Now determine a directory where you want to install and run Mallory. I like having it in my home Dir so thats where the rest of this tutorial will make reference to it.
> cd ~
> hg clone https://bitbucket.org/IntrepidusGroup/mallory
> cd mallory
> sudo ./mallory_install.sh
> sudo ./mallory_install.sh
The first time you run the installation script it will ask you to verify you have an internet connection. Once you verify you just run the same script again and it will download and install all of the dependencies.
Lets MiTM some traffic!!!
Finally the fun happens! We need to start the Mallory core process and then the Mallory GUI while the AP is running.> cd ~/mallory/current/src
> sudo python ./mallory.py
Open another terminal and type:
> sudo python ./launchgui.py
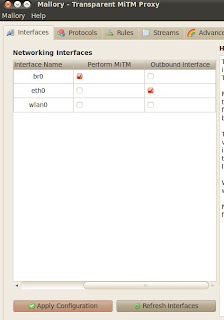
Once the GUI comes up Select the Interfaces Tab and ensure that br0 is checked for "Perform MiTM" and eth0 is checked for "Outbound Interface" and Click Apply.
Select the Protocols tab and uncomment the line starting with ssl_2 and Click Apply.
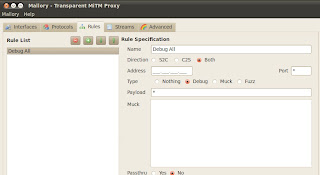
Click the Rules tab and ensure that Debug All is the current rule if not create it by copying the setting in the following ScreenShot.
Now Click on Streams and click "Intercept" and "AutoSend". After this you can navigate to some site on your phones browser and you should see the streams populating to the screen.
Now Mallory will send "Header: fake" instead of "Accept-Encoding: gzip,deflate" on all HTTP requests which prevents the server from sending a compressed response (i.e. you can read the responses it in Mallory's Streams tab now).
The Mallory CA is located in ~/mallory/current/src/ca/ca.cer. If your intercepting traffic on IOS you can just email this cert to yourself, open the attachment with the IOS mail client, and select install. Now you can intercept SSL traffic with IOS apps that do certificate checks (and almost all do). On Android devices you need to install this certificate into /etc/security/cacerts.bks. You will need to jailbreak the device to do this and you will need the android SDK. There are already alot of articles on this so i'm not going to go into detail here. Maybe in another post.
Thats it. Good Luck! :)
Additional Set Up
Strip Encoding
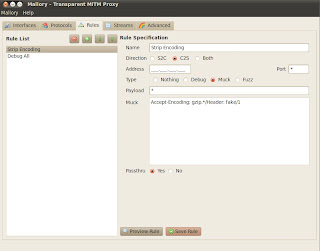
There are a few things your going to want to do here to really MiTM some traffic. First your going to want to create a rule that strips encoding on web pages since mallory does not automatically decode these like Burp Suite does.
- Select the Rules tab.
- Set the Name to "Strip Encoding".
- Direction C2S (Client to Server)
- The Type is Muck
- Enter Accept-Encoding: gzip.*/Header: fake/1 into the Muck textbox.
- Passthu = yes
- Move "Strip Encoding" to the top.
Install the CA Cert on a mobile device
The next thing you will want to do is add Mallory's CA cert to your device. This is how you can intercept SSL traffic without the mobile device giving you SSL warnings or some apps will not connect at all if the certs are not signed by a trusted CA.The Mallory CA is located in ~/mallory/current/src/ca/ca.cer. If your intercepting traffic on IOS you can just email this cert to yourself, open the attachment with the IOS mail client, and select install. Now you can intercept SSL traffic with IOS apps that do certificate checks (and almost all do). On Android devices you need to install this certificate into /etc/security/cacerts.bks. You will need to jailbreak the device to do this and you will need the android SDK. There are already alot of articles on this so i'm not going to go into detail here. Maybe in another post.
Thats it. Good Luck! :)






1 comment:
So aggressive blog i am really so nice post i am so inspired here could you more share here i will be back to you as soon as possible.
Thanks for sharing...
Wireless Access Point
Post a Comment